Warzone 1
Tool used: Brim, Wireshark, VirusTotal Miner
Scenario: You work as a Tier 1 Security Analyst L1 for a Managed Security Service Provider (MSSP). Today you’re tasked with monitoring network alerts. A few minutes into your shift, you get your first network case: Potentially Bad Traffic and Malware Command and Control Activity detected. Your race against the clock starts. Inspect the PCAP and retrieve the artifacts to confirm this alert is a true positive.
Network Analysis
Brim
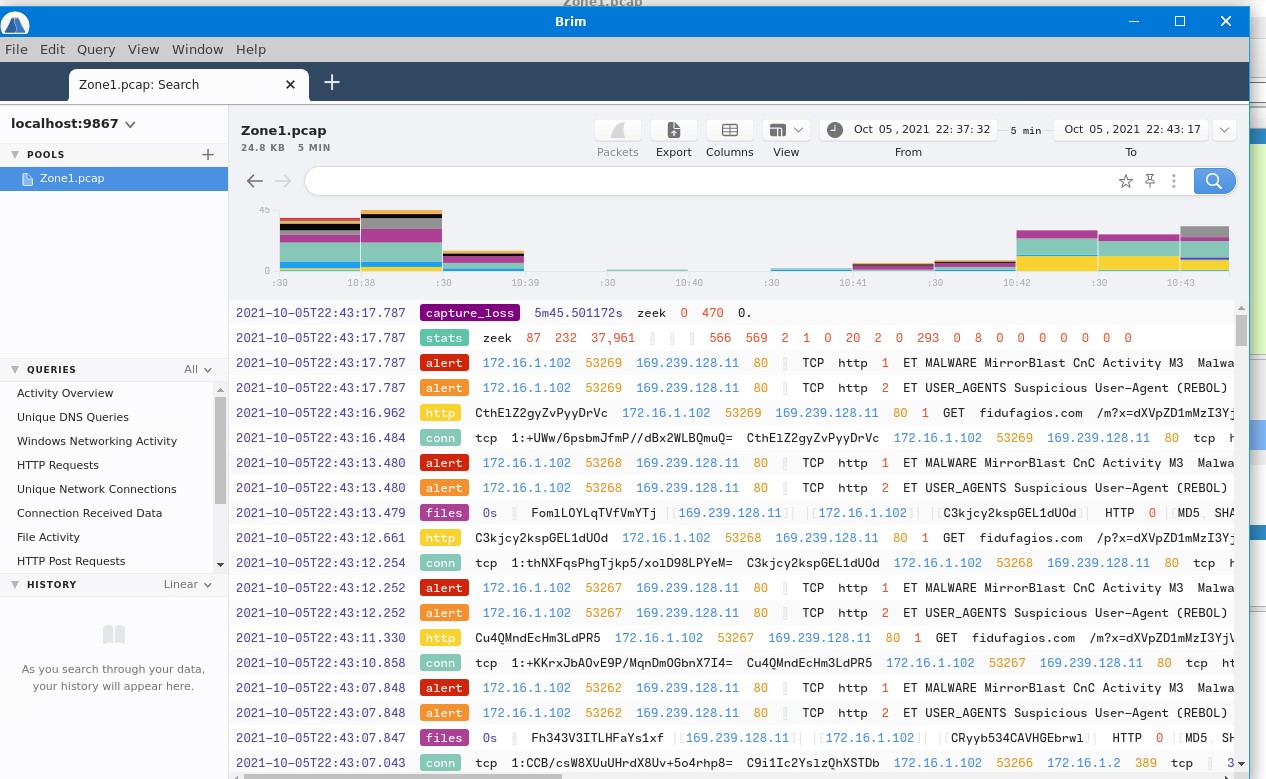
Brim Network Forensic Tool is used for large traffic log such as the pcap file. I opened the pcap file in brim to find information about the log. After the file loaded I can see overall information about the file unlike wireshark. Browsing through each row I can see a malware signature “ET MALWARE MirrorBlast CnC Activity M3” which had ‘ALERT’
Note: Defrag format is 10[.]10[.]10[.]10
VirusTotal
I did not know you can inspec IP addresses in virus total, after searching the Ip address 4 Tabs can be seen:
- Detection: I can see which vendor detected it as malicous.
- Details: I can see the basic properties, Last HTTPS certificate, and Google results
- Relations: I can see the passive DNS Replication, Communicating files, Files Referring, Historical whois lookups, Hisorical SSL certificates
- Community
MirrorBlast is a malware campaign, and the malware family.
Back to Brim
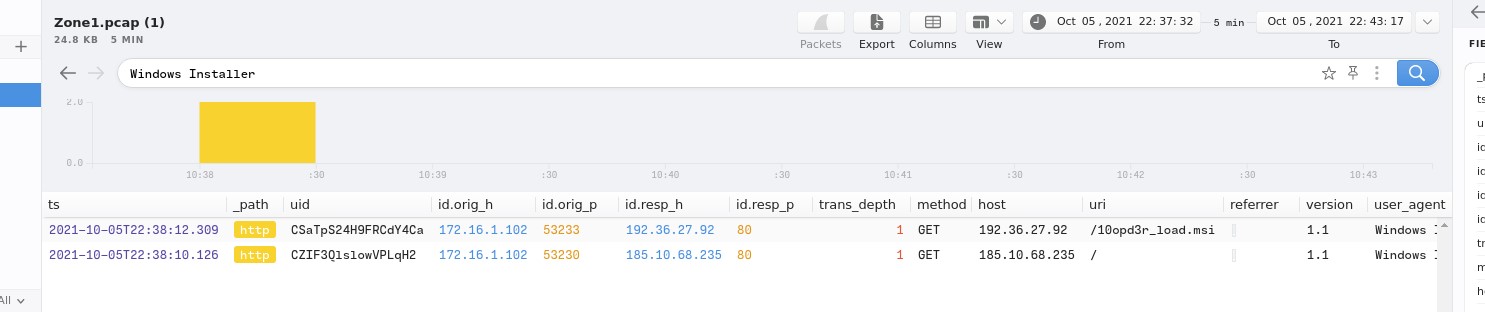
I can also see that after searching for the domain of the malware that majority of the file type listed is Windows installer.
After finding the malware name, and what its pretending to be the next question was finding two more ip addresses that are ssociated with the attack. This was easy, I used Brim to search for any ‘Windows Installer’ in the search bar and i found two ip addresses.
The next question was asking about the file names that were downloaded, i found one of the files easily and start looking for the other file. I pressed on the File Activity in the Queries and found the last file!
Locating the two files. I used the hint to know how to locate them it was by using follow > stream. I searched using the keyword ‘Windows Installer’ first, the MSI, finally I used a guide and seaeched c:\ to find the file directory and the extentions.