NIST Cybersecurity Framework
Introduction
There are several complex cybersecurity frameworks that can be utilized to construct a more effective security program and aid in guiding the organization to manage and mitigate risks. Organizations can employ the NIST framework to:
- Evaluate their existing cybersecurity posture
- Identify any gaps
- Prioritize necessary actions
- Formulate a roadmap to enhance their overall cybersecurity resilience.
There are several well-known frameworks, such as ISO 27001 and CIS Controls, among others. All of these frameworks offer valuable guidance for enhancing cybersecurity practices. However, my current focus is on the NIST framework, which consists of five core functions, an implementation tier, and profiles.
Components
(Functions)
The core consists of activities, desired outcomes, and relevant references that are universally applicable across the sector. This encompasses industry standards, guidelines, and best practices that can be effectively communicated and understood from an executive level down to the implementation and operational levels.
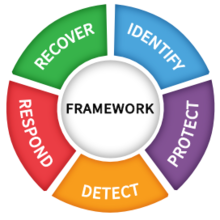
The core consists of 5 functions:
- Identify
- Protect
- Detect
- Respond
- Recover
You’ve identified that taking care of the organization’s assets is really important. One big thing you noticed is that some data that’s not being actively used isn’t properly protected. To make sure it’s protected, you’ve added measures to keep it locked up, like putting it in a digital safe (encrypting it). You’ve also set up a way to detect if anyone tries to mess with it without permission.
Now, the next step is being ready to respond if something goes wrong. If your watchful system notices anything fishy, you want to have a plan in place to take action and stop any potential problems from getting worse. It’s like having a team on standby to deal with things immediately.
Even though you’ve done a lot to be prepared and responsive, there’s still one more important thing: making sure that if something does happen, you can recover and bounce back quickly. Think of it like having a backup plan to get everything back to normal and running smoothly again. The better your plans for all these steps, the faster you can get things back on track.
Implementation Tiers (process)
The Implementation Tier assists the organization in evaluating and communicating their level of cybersecurity maturity and readiness. It helps them get a clear picture of where they currently stand in terms of putting the core functions of the framework into action. Moreover, it offers a guide for how they can enhance their practices and move forward effectively.
There are four implementations Tiers
| Tiers | Risk Management Process | Integrated Risk Management Program | External Participation |
|---|---|---|---|
| Partial | Risk Management Process is not Formalized and process is not well defined and AD hoc approach for risk or ractive manner | There is limited awareness of cybersecurity risk at the organizational level and inconsistencies in security measurement implemented across the organization | inconsistencies in security measurement implemented across the organization. Not aware to supply chain risks |
| Risk-Informed | Risk Management Process is approved by management but may not be established as organizational-wide policy | There is an awareness of cybersecurity risk at the organizational level, but an organization-wide approach to managing cybersecurity risk has not been established. Identified and prioritzed critical assests, vulenerabilities, and threats | Orgaization does collaborate but may not share information wth others and they are aware of supply chain risks |
| Repeatable | Risk Management Process is fromally approved and expressed as policy and its updated when changes in bsuiness or mission requirment changes or when the threat and technology changes | organizational-wide approach to manage the risk. Risk-informed policies, processes, and procedures are defined, implemented as intended, and reviewed | It collaborates with and receives information from other entities regularly that complements internally generated information, and shares information with other entities. The organization is aware of the cyber supply chain risks. Usually acts formall upon supply chain risk |
| Adaptive | The organization adapts its cybersecurity practices based on previous and current cybersecurity activities, including lessons learned and predictive indicators. Actively adapts to a changing threat and technology landscape and responds in a timely and effective manner to evolving, sophisticated threats. | organization-wide approach to managing cybersecurity risk that uses risk-informed policies, processes, and procedures to address potential cybersecurity events. | The organization shares that information internally and externally with other collaborators. The organization uses real-time or near real-time information to understand and consistently act upon cyber supply chain risks associated. Communicates proactively, using formal (e.g. agreements) and informal mechanisms to develop and maintain strong supply chain relationships. |
By knowing where they currently stand and setting goals to move up in the tiers, the organization can make their cybersecurity stronger and align their efforts with the industry best practices and communication their cybersecurity maturity to stakeholder and partner
Profiles (Attributes)
Profiles refer to customized sets of cybersecurity rules and safeguards that are chosen and put in place to match an organization’s comfort level for risk, business goals, and rules it needs to follow. An organization can use several profiles.
Profiles help outline how things are being done now and how they should be done in the future for specific cybersecurity actions. Looking at the differences between these can show where problems might be, and then a plan can be made to fix those problems.
- Current state: What’s happening right now as a result of the actions taken.
- Desired state: The result that needs to happen or be reached.